A New Way to Examine and Tackle Mobile Ad Fraud
Anti-fraud solutions will help to advance the entire mobile ad ecosystem.

Opinions expressed by Entrepreneur contributors are their own.
Fraud might seem like an enigmatic problem, with no obvious remedy to stop it from taking your campaign budgets.
But, in fact, mobile ad fraud is somewhat limited in the operations or, how it can work. Though fraudsters are always developing new exploits to steal an app’s marketing budget, or to circumvent fraud prevention solutions, that doesn’t mean the underlying systems vary. Such a distinction is important when trying to develop a foolproof solution against the biggest challenge in the mobile marketing industry today.
At Adjust, we think about fraud differently. We view exploits, such as SDK Spoofing, as “methods,” or ways in which a fraudster can operate in order to steal. But, at its root cause, mobile ad fraud can only work in one of two established structures, or “types.”
This viewpoint may come across as an unfamiliar mindset, even unnecessary to some. However, we believe the problem of mobile ad fraud, once defined, can be dealt with much more effectively. Instead of arguing over semantics, the industry as a whole can move forward, dealing with fraud in a more cooperative way.
There are ultimately only two types of fraud.
In all types of fraud, a fraudster can spoof one (or both) of two types of “signals’ used in attribution. The two types of signals they can spoof are ad engagements (like views or clicks) and app activities (like installs, sessions and events).
Thus, we’ve created a distinction between types of fraud that spoof ad engagements or the user’s in-app activity. The former is known as Spoofed Attribution. The latter is called Spoofed Users.
Related: 5 Psychological Reasons ‘Social Proof’ Beats Everything Else in Marketing
Why make this distinction?
Whenever you discover a new method of fraud, it’s best to start an investigation into it by first identifying which type of signal this form of fraud wants to exploit.
For instance, one method of Spoofed Attribution began as “Click Spamming.’ As time passes you may discover more advanced methods — “Click Injection’ among them. Both methods result in stealing attribution, but they work in different ways. Don’t worry if you don’t know these both types of fraud, we cover that later in more detail.
By understanding that the two work within the same system, it becomes easier to apply solutions that deal with both. Basing the two in a single definition – Spoofed Attribution – it is much simpler to work in terms of fraudsters stealing attribution, while not getting them mixed up with other schemes.
Defining ad fraud – but to what purpose?
Essentially, in the process of trying to stamp out each individual method, certain patterns become identifiable. Instead of asking, “Is this fraud?” you should be asking:
What is the method of this fraud?
How did they get this user activity into our system?
How does Click Spamming really work?
If you begin by stating that there is a problem, and then look at the individual methods applied, you’ll gain a more assured understanding. Follow these proactive steps:
This is that method
This is the countermeasure
This is the yes-no filter
Fraud types
Combining the previously mentioned spoofed signals, here’s a visual matrix:

Everything in Type I is considered genuine traffic, where real users are driven to interact with an app by an advertisement with which they have actually engaged.
Type II describes Spoofed Attribution — where a fraudster spoofs ad engagements for real users, with the aim of stealing credit from a user that either organically interacted with the app or was driven by another legitimate advertisement. This type is also known as “stolen attribution’ or “poaching.”
Type III and IV defines Spoofed Users: this type of fraud focuses on simulating the behavior of user in-app activity. By spoofing installs and events for non-existent users, fraudsters can steal ad budgets aimed at rewarding app-based conversions. “Botting,” “bots” and fraud related to “fake users” are all associated with this type.
Currently, fraudsters can easily fake ad engagements for any users they’ve fabricated. So, whenever spoofed app activity appears, it’s always coupled with fraudulent engagement data. For the sake of simplicity, types III and IV have been grouped together.
When discussing fraud, it’s useful to think of these “types” (such as Spoofed Attribution) as the “what,” and “methods” (like Click Spam) as the “how.”
Related: How to Be Invisible Online — Without Going Off the Grid (Infographic)
Fraud methods
So, what do these “methods’ look like in practice? Splitting them into their respective types, you gain more clarity into what each fraud method does.
Methods of Spoofed Attribution include Click Spam and Click Injection. With Spoofed Users where the activity is faked, there are Simulators, Device Farms and SDK Spoofing. When applying our above matrix, the configuration of fraud looks like this:

Let’s cover each type in a little more detail.
Spoofed Attribution
Spoofed ad engagements started out with simple Click Spamming and its variations like “click stacking,” “views as clicks” or “preloading.” These methods function by targeting as many clicks to an attribution company as possible and gaining attribution for users by randomly matching device IDs or fingerprints.
Advanced methods (like Click Injection) create fake clicks during the download of an app, claiming attribution with an impossible to beat “last click.”
Spoofed Users
The first cases of Spoofed Users detected involved simulators on cloud computing services running Android apps that were pretending to be real users. On iOS, device farms exist in southeast Asian countries where real devices and actual humans created non-genuine app activities.
Recently, there’s a much more devious method: SDK Spoofing. This cuts the cost for creating fake user interactions by only faking the requests made from an app to servers of attribution companies and app publishers, instead of actually running the app. Fraudsters have broken encryptions and hashed signatures, which has led to an arms race between fraudsters and researchers.
Simulators, cheap labor and bots can all be used to create fraudulent app activities. They are all different methods used to commit the same type of fraud.
Related: Giving Advertisers a Way to Bypass Facebook Click Fraud
What is fraud prevention?
Finally, it’s important to examine the lack of distinction between fraud solutions, and exactly how you apply a methodology to create a stronger system.
A lot of confusion exists among prevention, detection and rejection – often to the detriment of advertisers who want to run campaigns without interference. The industry often uses detection, prevention and rejection in the same context interchangeably. This creates uncertainty from a lack of expertise, which is advanced maliciously to keep the market in an ongoing state of confusion.
Fraud prevention is the act of rejecting attribution to known methods of fraud.
The chart below illustrates an important flow to follow for detecting a type of fraud, then researching the method used before finally creating a logical filter for its unique characteristics.
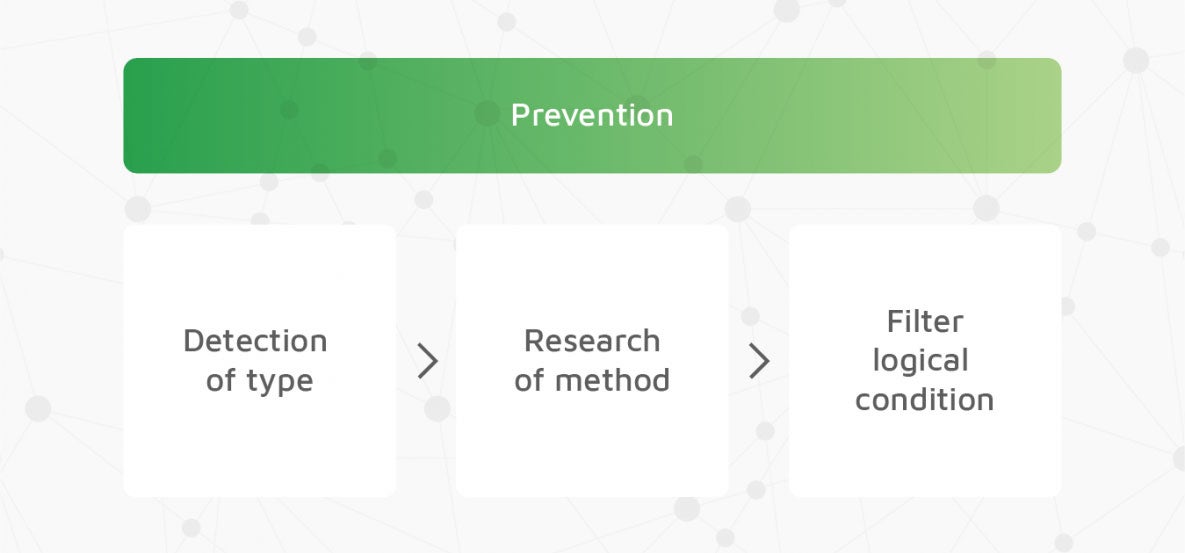
When applying this prescribed definition of fraud prevention, you’ll find that only attribution companies are in a position to apply filters effectively. Third-party tools can only show detection metrics after the fact, unless an attribution company allows them to interfere with the attribution.
Fraud prevention should not just be a marketing ploy, or a means to muddy the water — it’s a serious responsibility. If done correctly, anti-fraud solutions will help to advance the entire mobile ad ecosystem. If done without the proper attention to detail and the research necessary, it will end up as the snake oil of our industry.
Fraud might seem like an enigmatic problem, with no obvious remedy to stop it from taking your campaign budgets.
But, in fact, mobile ad fraud is somewhat limited in the operations or, how it can work. Though fraudsters are always developing new exploits to steal an app’s marketing budget, or to circumvent fraud prevention solutions, that doesn’t mean the underlying systems vary. Such a distinction is important when trying to develop a foolproof solution against the biggest challenge in the mobile marketing industry today.
At Adjust, we think about fraud differently. We view exploits, such as SDK Spoofing, as “methods,” or ways in which a fraudster can operate in order to steal. But, at its root cause, mobile ad fraud can only work in one of two established structures, or “types.”





